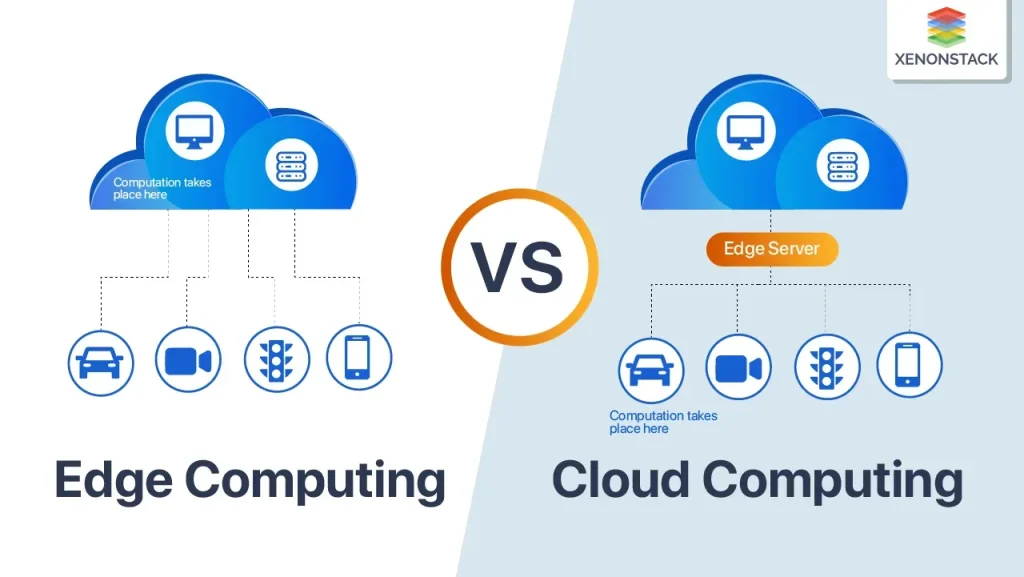
Cloud technology and edge computing are reshaping how organizations store, process, and protect data at the speed of business. As data volumes grow and milliseconds matter, edge computing speed becomes a defining factor in real-time monitoring, automation, and user experiences. To keep data safe across distributed locations, organizations adopt cloud security best practices that span identity, encryption, and continuous monitoring. A thoughtful approach to scalability in cloud and edge ensures workloads can shift between centralized clouds and local endpoints without complexity. A practical pattern like hybrid cloud edge architecture enables real-time actions at the edge while preserving governance, analytics, and IoT edge computing benefits.
Viewed through an alternative lens, this approach blends centralized cloud capabilities with nearby processing power to shorten the data-to-action path. It emphasizes proximity processing, edge analytics at gateways, and resilient data pipelines that empower autonomous decision-making closer to sources. This pattern mirrors terms like distributed computing at the edge, intelligent edge gateways, and near-edge architectures, connecting local responsiveness with cloud-grade analytics. Organizations adopt a hybrid topology that keeps latency-sensitive workloads at the edge while leveraging cloud-based governance, storage, and model deployment.
Cloud technology and edge computing: Enhancing edge computing speed and cloud security best practices
Cloud technology and edge computing accelerate decision-making by bringing compute closer to sensors and devices, delivering edge computing speed that makes real-time monitoring and control feasible. This proximity enables faster alerts, tighter feedback loops, and improved safety in industrial, healthcare, and consumer applications, reinforcing the IoT edge computing benefits where latency matters.
By applying cloud security best practices at edge locations—encryption in transit and at rest, secure boot, identity management, and continuous monitoring—organizations preserve governance while expanding processing horizons. A unified security model across cloud and edge helps ensure data visibility, policy enforcement, and risk management as workloads migrate between layers.
Cloud technology and edge computing: A practical guide to hybrid cloud edge architecture and scalable governance
Hybrid cloud edge architecture offers a practical pattern to scale responsibly. Edge devices handle low-latency, local analytics, while the cloud layer coordinates data governance, centralized analytics, and long-term storage. This model supports scalability in cloud and edge through elastic resource usage, intelligent data routing, and consistent policy application across sites.
IoT edge computing benefits become tangible when you pair edge intelligence with robust data governance, observability, and security controls. Start with use cases that benefit from edge processing, then extend insights to cloud-scale analytics, model training, and cross-site collaboration. This approach unlocks resilient, scalable operations and faster time-to-value for connected products and services.
Frequently Asked Questions
How do cloud technology and edge computing collaborate in a hybrid cloud edge architecture to improve edge computing speed?
In a hybrid cloud edge architecture, latency-sensitive processing happens at the edge while the cloud handles heavier analytics, data aggregation, and centralized governance. This combination reduces round-trips, lowers bandwidth usage, and boosts edge computing speed with near-real-time responses. Key patterns include edge-native processing pipelines, intelligent data routing, and coordinated policy management, backed by secure communication and continuous monitoring across both layers.
What cloud security best practices should guide the deployment of cloud technology and edge computing to maximize scalability in cloud and edge and unlock IoT edge computing benefits?
Apply cloud security best practices across cloud and edge locations: implement identity and access management, encryption at rest and in transit, secure boot and attestation for edge devices, and regular vulnerability assessments; adopt zero-trust architectures, centralized key management, and end-to-end monitoring. This approach supports scalability in cloud and edge and unlocks IoT edge computing benefits—faster alerts, local decision-making, and resilient operations—while maintaining consistent policy enforcement, data governance, and threat detection across the hybrid environment.
| Aspect | Key Point | Impact / Benefit |
|---|---|---|
| Speed and Latency | Edge computing brings processing closer to data sources, reducing travel time to data centers. | Real-time monitoring, faster responses, and lower bandwidth usage. |
| Security | Extend cloud security practices to the edge with hardware security modules, secure boot, encryption, and zero-trust policies. | Consistent security posture across cloud and edge. |
| Scalability | Elastic deployment, intelligent data routing, and governance that scales with the organization. | Seamless workload migration and cost efficiency. |
| Hybrid Cloud Edge Architecture | Edge handles latency-sensitive processing; cloud handles aggregation, analytics, governance. | Fast local responses with centralized analytics and governance. |
| IoT Edge Computing Benefits | Real-time alerts, energy efficiency, and resilience; edge enables near real-time predictive maintenance. | Improved uptime and proactive maintenance; cloud supports long-term analysis. |
| Security-First Design | IAM, encryption, secure development, regular assessments, least-privilege access, and monitoring across cloud/edge. | Reduced risk and better breach containment. |
| Data Governance & Compliance | Data classification, retention, lineage, and data sovereignty considerations across locations. | Compliance and rapid localized decision-making. |
| Implementation Best Practices | Use-case selection, map data flows, standardized APIs, modular architecture, secure-by-design, observability. | Faster ROI and maintainability. |
| Challenges & Considerations | Interoperability, total cost of ownership, data consistency, vendor lock-in, operational complexity. | Need for mitigation strategies and careful planning. |
| The Future | AI-forward workloads, 5G/6G capabilities, and smarter serverless edge offerings. | More capable, autonomous edge with centralized governance. |
Summary
Conclusion: Cloud technology and edge computing are complementary layers of a modern, resilient IT strategy. By bringing intelligence closer to the data source, organizations can achieve edge computing speed for real-time decisions, while maintaining robust cloud security and scalable governance. A well-designed hybrid cloud edge architecture enables fast, local responses alongside centralized analytics, governance, and long-term storage. IoT edge computing benefits—faster alerts, energy efficiency, and resilience—are amplified when combined with scalable cloud services and strong security-first practices. Successful implementations start with clear objectives, data-flow mapping, standardized interfaces, modular design, and strong observability across the distributed stack. As technology evolves, those embracing the blend of cloud technology and edge computing will unlock faster insights, better customer experiences, and greater resilience in a data-driven world.